Admin
My contact centre is failing to create
In Amazon Connect, ensure customer Profiles are either NOT enabled (NEONNOW will enable), OR if enabled, ensure you have set a domain name of amazon-connect-connect-instancealias, e.g. amazon-connect-myinstance123
Where is customer data stored?
Most customer data is stored within the AWS Account that holds the Amazon Connect instance. This provides full visibility to you as a consumer of NEONNOW. You can see data, and apply custom retention rules. However, to use our SaaS platform, certain data must be stored within our product.
Note, all data is encrypted at rest and in Transit.
Breakdown of Customer data storage in NEONNOW
- Admin user details - NEONNOW user information such as name, organisation etc.
- Agent interaction history - Call information including contact ID, call time, phone number, connection type etc.
- Subscription data - Subscriber information such as business name, point of contact name, product, number of users, phone number, email address. Information about any NEONNOW instances, such as permissions. Organisation information, such as microsoft integration credentials.
- Agent status changes - Stores a minute-buy-minute record of agent statuses, including changes in status
- Agent information - Email address (SSO), Name, Amazon Connect username, roletype
- Product Usage - Stores aggregated active agent minutes usage, that’s created by looking at agent status changes.
- Billing Log - Stores Amazon Marketplace API responses after we send billing dimensions/records for subscribed customers.
- Modules - Admin added modules displayed in the product. (e.g. custom iframes)
- Contacts - Personal contacts/organisation contacts and any SCIM synchronised contacts - Names, Email addresses, Phone numbers, SCIM user IDs, Job titles
- Schedules - Admin added custom date schedules used by contact flows in Amazon Connect.
- Operational Parameters - Admin added parameters used by contact flows in Amazon Connect
- Email rules / addresses - Stores source customer email address for routing and the name of the associated AWS SES email identity
- Templates - Rich text templates used for chat and SMS
- Email records - A record of all inbound and outbound messages to the email channel. Does not store message content or attachments.
- From email address
- Date
- Subject
- Type
- To email address
- Organisation Branding - Customer image assets for logos and favicons
- Conversation Records (Chat) - Tracks external conversations and their corresponding Amazon Connect contact relationship. Does not store any messages.
Breakdown of Customer data storage in the Customer AWS Account
The following data is the additional data that NEONNOW will store within the Customer's AWS Account.
- Emails & Email Attachments (inbound + outbound) - Emails and attachments if the email channel is enabled in NEONNOW. Stored in 2 Amazon S3 buckets (one for content + one for attachments) per NEONNOW instance, secured with Amazon S3 managed keys (Server-side encryption with Amazon S3 managed keys (SSE-S3)). Default no deletion - can be set up on a per customer basis.
For general Amazon Connect data storage, see here
How long is my data stored for?
All data stored within NEONNOW is retained when a customer unsubscribes, and only deleted on decommission of customer tenant. Unsubscribed tenants will be tiedied up and decomissioned at regular intervals. Please reach out to your account manager in the event you would like all data pertaining to your tenant removed.
How is my data secured?
All data stored within NEONNOW is Encrypted at Rest and in Transit. Data at rest is encrypted using 256-bit Advanced Encryption Standard (AES-256) with AWS-Managed Keys. In May 2022, AWS KMS changed the rotation schedule for AWS managed keys from every three years (approximately 1,095 days) to every year (approximately 365 days).
What additional services are deployed to my AWS Account (and how much will they cost)?
Under a base-build of NEONNOW, the only additional billable services in your Account will be an IAM Role. Note, IAM does not have a direct cost.
With the NEONNOW Email Module, the following will be introduced (note this requires manual setup and is not available self-service)
- AWS SES - please refer to AWS SES pricing here
- AWS S3 - please refer to the S3 pricing here. S3 usage will entirely depend on the number of emails sent and received, attachment size, and retention rules applied.
As an example, assuming an average email size of 100KB, and a daily volume of 1000 emails, with 36 month retention, this would trend up to a monthly storage requirement of 105GB, equating to US$2.42/month. This would result in a monthly SES cost of US3.10/month.
With the NEONNOW Reporting Module, the following will be introduced (note this requires manual setup and is not available self-service):
- QuickSight - QuickSight pricing can be found [here] (https://aws.amazon.com/quicksight/pricing/). Depending on how many users are required - Reader or Author user charges will apply
- Kinesis & Kinesis Firehose - CTR and Agent Stream is required to be set up - see here and here
- Athena - Athena is required for Quicksight integration - see here
- S3 - for stored Athena query data here
The amount of data being processed and thus required for the reporting solution is dependant on the number of interactions, the number of interactions within the contact centre etc. As an estimate, for a 300 seat contact centre, the reporting solution would typically add approximately US$500/month of charges within your AWS Account.
How can I reduce the IAM role created to least privilege?
The default IAM role created during the deployment process is restricted to the following services:
- connect:* (Connect) - used to manage Amazon Connect APIs, such as users, Queue Metrics, quick connects etc.
- profile:* (Connect customer profiles) - used to manage Amazon Connect customer profiles
- quicksight:* (Amazon Quicksight) - used to integrate with the Quicksight for Reporting embedding
- ses:* (Amazon SES) - used to orchestrate SES for the Email platform
- s3:* (Amazon S3) - used for storage of emails content
- kms:* (AWS Key Management Service) - used for securing Customer profiles with custom keys
- bedrock:* (Bedrock) - used for generative AI features
It is possible to restrict this as follows to adhere to AWS best practices of least-privilege. To modify, navigate to the IAM role created and updated the attached policy as follows. Replace specific resources and regions relevant for your deployment.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "Allow Connect",
"Effect": "Allow",
"Action": [
"connect:ListQuickConnects",
"connect:ListQueues",
"connect:GetMetricData",
"connect:GetCurrentMetricData",
"connect:UpdateContactAttributes",
"connect:PutUserStatus",
"connect:StartContactStreaming",
"connect:StartChatContact",
"connect:ListContactFlows",
"connect:StartTaskContact",
"connect:ListUsers",
"connect:ListRoutingProfiles",
"connect:ResumeContactRecording",
"connect:SuspendContactRecording",
"connect:StopContactRecording",
"connect:UpdateAgentStatus",
"connect:CreateAgentStatus",
"connect:AssociateApprovedOrigin",
"connect:DisassociateApprovedOrigin",
"connect:CreateQuickConnect"
],
"Resource": [
"arn:aws:connect:ap-southeast-2:111111111111:instance/7bd05fb6-f295-4f56-af74-81f41af67522"
]
},
{
"Sid": "Allow Quicksight",
"Effect": "Allow",
"Action": [
"quicksight:GenerateEmbedUrlForRegisteredUser"
],
"Resource": [
"arn:aws:quicksight:ap-southeast-2:111111111111:user/2222222222"
]
},
{
"Sid": "Allow SES",
"Effect": "Allow",
"Action": [
"ses:GetIdentityVerificationAttributes",
"ses:ListIdentities",
"ses:CreateReceiptRule",
"ses:CreateReceiptRuleSet",
"ses:VerifyEmailAddress"
],
"Resource": []
},
{
"Sid": "Allow S3",
"Effect": "Allow",
"Action": [
"s3:CreateBucket",
"s3:PutBucketPolicy",
"s3:PutLifecycleConfiguration"
],
"Resource": []
},
{
"Sid": "Allow Bedrock",
"Effect": "Allow",
"Action": [
"bedrock:InvokeModel"
],
"Resource": [
"arn:aws:bedrock:ap-southeast-2::foundation-model/ai21.j2-ultra-v1"
]
},
{
"Sid": "Allow KMS",
"Effect": "Allow",
"Action": [
"kms:CreateKey",
"kms:CreateGrant"
],
"Resource": []
},
{
"Sid": "Allow Amazon Connect Customer Profiles",
"Effect": "Allow",
"Action": [
"profile:SearchProfiles",
"profile:ListProfileObjects",
"profile:DeleteProfile",
"profile:CreateProfile",
"profile:PutProfileObjectType",
"profile:PutIntegration",
"profile:GetDomain",
"profile:CreateDomain",
"profile:UpdateProfile"
],
"Resource": [
"arn:aws:profile:ap-southeast-2:111111111111:domains/SampleDomainName"
]
}
]
}
What backups are applied to data stored in my AWS Account?
For your AWS account hosting Amazon Connect, it is your responsibility to create backups if this aligns with your DR strategy. Note, all data is stored in S3 on customer accounts, and has a very high availability (99.99%) and durability (99.999999999%) figures.
To set up backup for each of the following buckets:
- Email content bucket - will have a name such as neon-emails-tenantid-instancename
- Email attachments bucket - will have a name such as neon-emails-attachments-tenantid-instancename
- Amazon connect chat attachments bucket - defined by the user when enabling Amazon Connect chat attachments.
Enabling versioning on buckets - Amazon Simple Storage Service
Enabling lifecycle method on S3 bucket to manage excess cost associated with object versioning:
- Sign in to the AWS Management Console and open the Amazon S3 console at https://console.aws.amazon.com/s3/.
- In the Buckets list, choose the name of the bucket that you want to enable versioning for.
- Choose Management.
- Under Lifecycle Management, choose Create New Lifecycle.
- Choose the options as shown in the screenshot, and then choose Save changes. Select the number of days you wish to keep the data
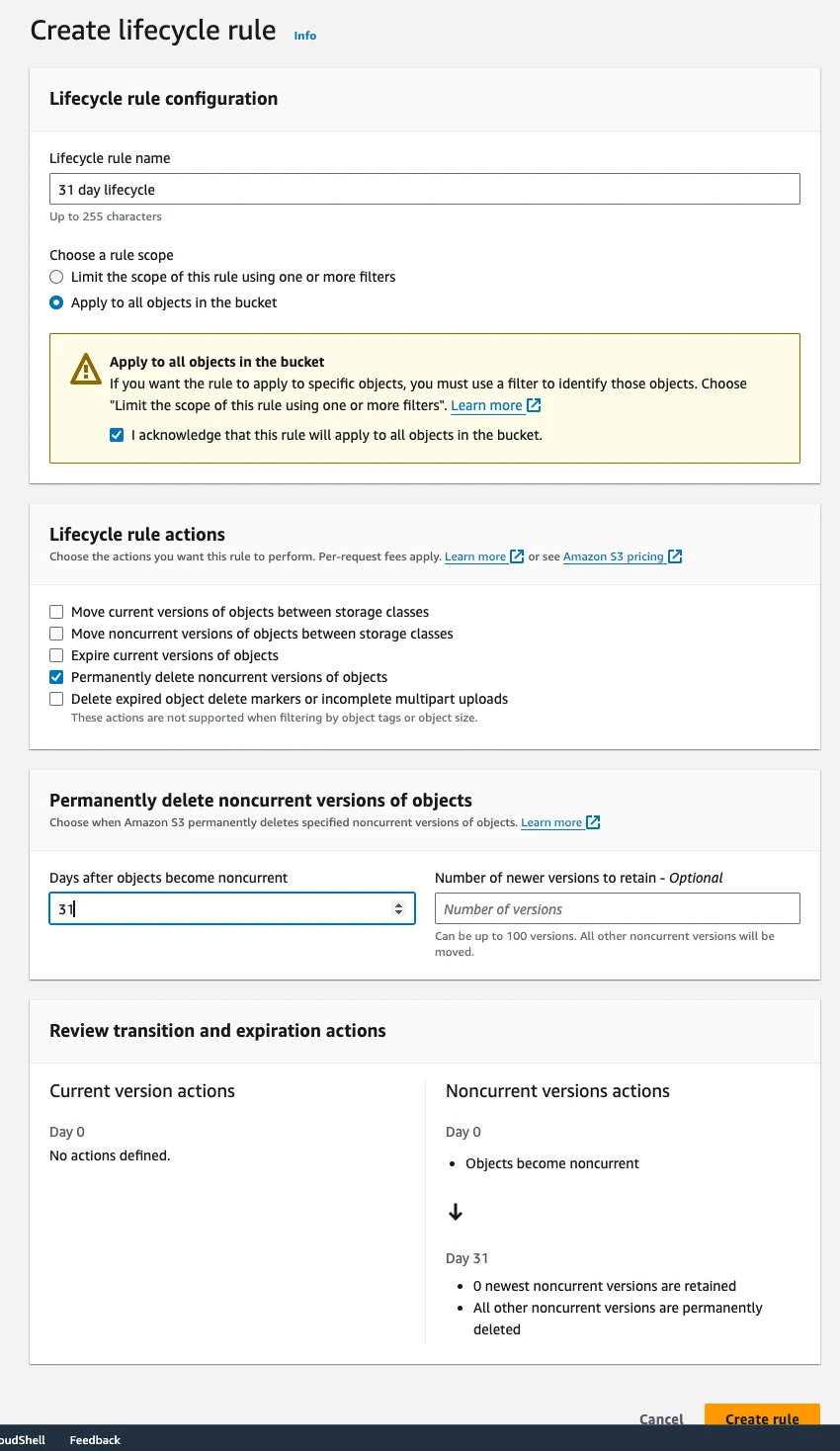
Enable AWS Backup for continuous backups
- Sign in to the AWS Management Console and open the Amazon Backup console at https://console.aws.amazon.com/backup/.
- Click on Create Backup Plan
- Create a backup plan with the following configuration:
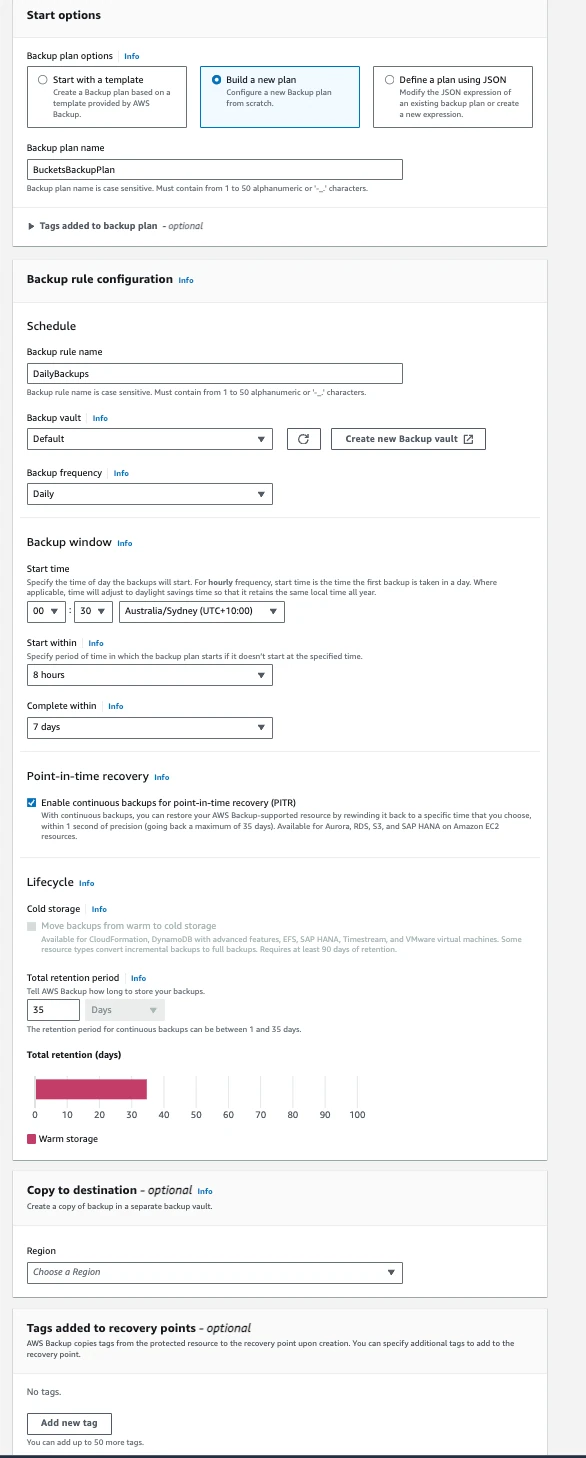
- Select the newly created Backup Plan, and click on Assign Resources under Resource Assignments
- Choose the given configuration and select the buckets that need to be backed up, and click on Save
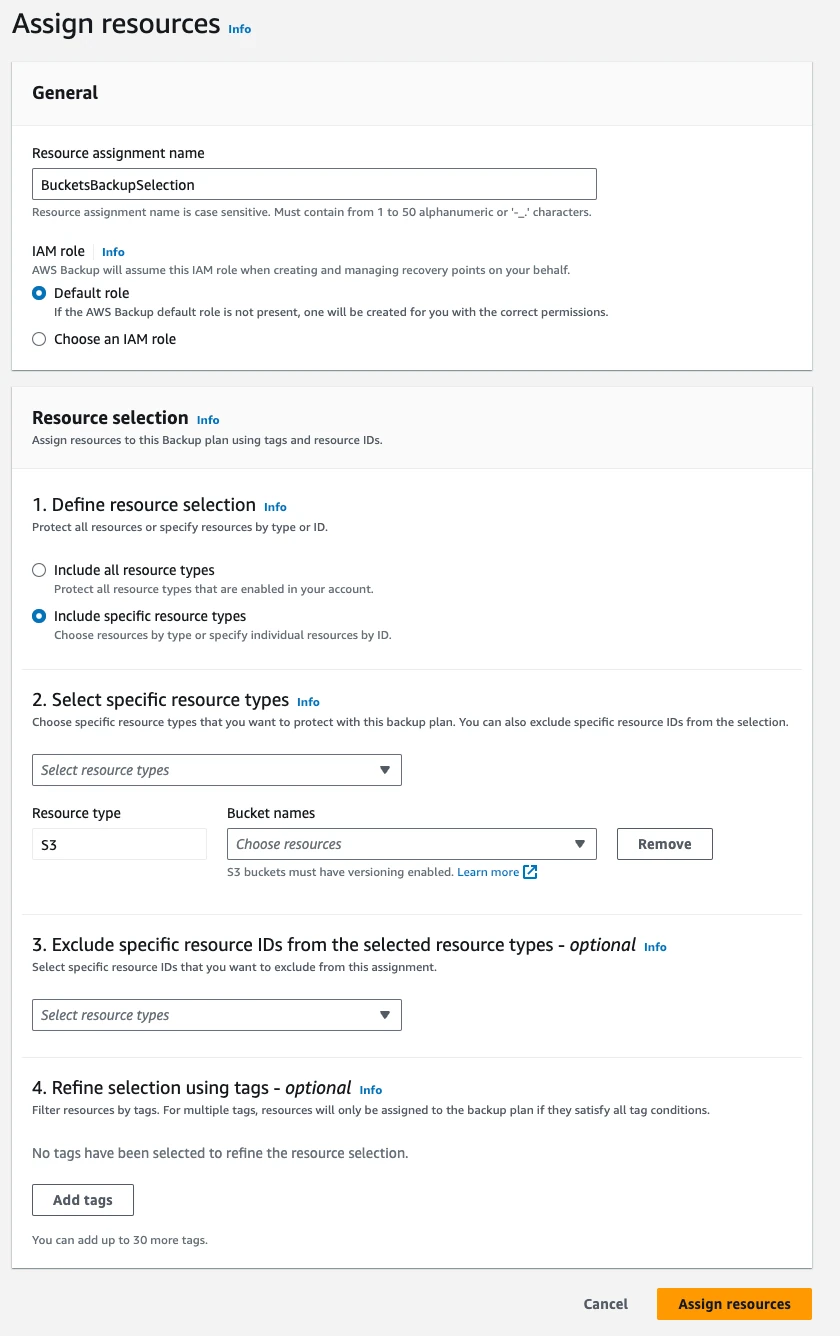
- Backups are now enabled for the chosen buckets in you AWS account.
Status Page
To stay informed about the current status of our applications and services, please visit our Status Page. This page provides real-time updates on system performance, planned maintenance, and any incidents affecting service availability.